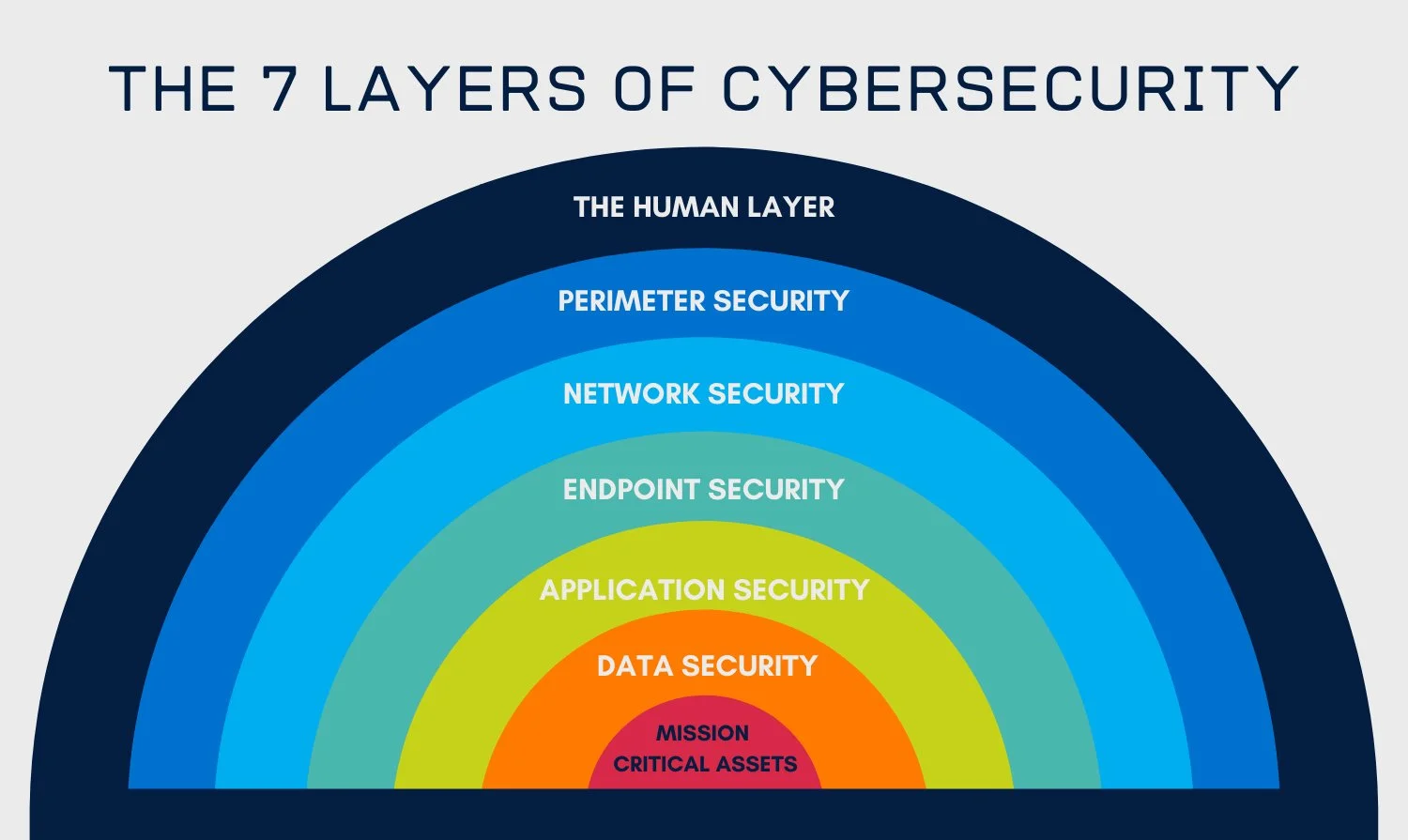
The Multi-Layered Approach to Cybersecurity
In today’s digital landscape, cyber threats are becoming more sophisticated, making it essential for businesses to implement a multi-layered cybersecurity strategy. A single security measure is no longer enough to protect against evolving cyber threats. Instead, organizations must adopt a comprehensive approach that safeguards every layer of their IT infrastructure.
One of the best ways to achieve this is by partnering with a Managed IT Provider. With expert knowledge, continuous monitoring, and cutting-edge security solutions, a Managed IT Provider can help businesses build a robust cybersecurity defense. Let’s explore the different layers of a multi-layered cybersecurity strategy and how partnering with an IT provider simplifies the process.
The Key Layers of a Multi-Layered Cybersecurity Approach
1. Perimeter Security
The first line of defense against cyber threats is perimeter security. This includes firewalls, intrusion prevention systems (IPS), and secure web gateways that filter out malicious traffic before it reaches the internal network.
2. Network Security
Once inside the network, it’s crucial to monitor and control traffic to prevent unauthorized access. Solutions such as network segmentation, VPNs, and zero-trust policies ensure only authorized users and devices can access sensitive information.
3. Endpoint Security
Every device connected to a business network—desktops, laptops, smartphones, and tablets—is a potential entry point for cyber threats. Endpoint security solutions like antivirus software, endpoint detection and response (EDR), and patch management help protect these devices.
4. Email Security
Phishing remains one of the most common cyberattack methods. Email security measures, such as advanced spam filters, email encryption, and employee awareness training, can significantly reduce the risk of falling victim to email-based threats.
5. Application Security
Many cyberattacks target vulnerabilities within software applications. Regular software updates, security patches, and web application firewalls (WAF) help keep business applications secure from exploits and breaches.
6. Identity and Access Management (IAM)
Ensuring that only authorized personnel have access to critical systems is essential. IAM solutions, such as multi-factor authentication (MFA), role-based access control (RBAC), and single sign-on (SSO), help strengthen access security.
7. Data Protection and Encryption
Sensitive business data should be encrypted both in transit and at rest to prevent unauthorized access. Backup solutions and disaster recovery plans also ensure data remains available in case of ransomware attacks or system failures.
8. Security Monitoring and Incident Response
Continuous security monitoring, security information and event management (SIEM) systems, and threat intelligence help detect and respond to security incidents in real-time, reducing potential damage.
9. Employee Awareness and Training
Human error is one of the biggest cybersecurity risks. Regular training programs ensure employees recognize phishing attempts, follow secure practices, and adhere to company security policies.
Why Partnering with a Managed IT Provider Makes Cybersecurity Easier
Implementing a multi-layered cybersecurity approach requires expertise, resources, and constant vigilance. This is where a Managed IT Provider becomes invaluable. Here’s why:
Expertise & Advanced Technology: Managed IT Providers have access to the latest security technologies and employ cybersecurity experts who stay ahead of emerging threats.
24/7 Monitoring & Response: Continuous monitoring ensures potential threats are identified and mitigated before they cause harm.
Cost-Effective Security Solutions: Maintaining an in-house cybersecurity team is expensive. A Managed IT Provider offers enterprise-grade security at a fraction of the cost.
Proactive Threat Management: Instead of reacting to threats after they occur, Managed IT Providers implement proactive measures to prevent cyberattacks.
Regulatory Compliance: Many industries require businesses to meet strict cybersecurity regulations. A Managed IT Provider ensures compliance with industry standards such as HIPAA, GDPR, and CMMC.
Focus on Core Business Operations: Outsourcing cybersecurity to experts allows businesses to focus on growth and operations without worrying about security threats.
Secure Your Business with a Multi-Layered Cybersecurity Approach
A single security solution is not enough to protect against today’s complex cyber threats. A multi-layered cybersecurity approach provides comprehensive protection, reducing the risk of data breaches, ransomware attacks, and unauthorized access. By partnering with a Managed IT Provider, businesses gain access to top-tier security solutions, expert guidance, and proactive threat management—making cybersecurity easier and more effective.
Don’t wait until a cyberattack disrupts your operations. Strengthen your business’s security posture today with a Managed IT Provider and stay ahead of evolving threats.
Ready to Enhance Your Cybersecurity?
Contact us today to learn how our Managed IT Services can help secure your business from cyber threats.